Security
Lifting the lid on the risk of ‘insider threats’ at airports
Airports Council International (ACI) recently published a new handbook on ‘insider threats’- airport personnel who exploit their positions to commit terrorist attacks and other devastating crimes. To find out more, Heidi Vella spoke to the handbook’s co-author and ACI head of security and facilitation Nathalie Herbelles
Attacks at airports or on aircraft are fortunately still very rare. But they do still happen and sometimes they are facilitated by airport staff who have trusted access to critical safety elements or information.
As history shows, ‘insider threats’, as this risk is known, are persistent and evolving. Not only do they include the potential for deadly terrorist attacks but also financial misconduct, espionage, cyber and other crimes. Similarly, it’s not only bad actors blackmailing or exploiting personnel or staff members gone rogue that might facilitate or carry out such an attack but people with criminal intent actively seeking employment within an airport.
The threat vector landscape is complex, as the Airports Council International (ACI) ‘Addressing Insider Threat Handbook’, which was officially launched at its annual Asia-Pacific/World conference in April, details. However, fortunately, there are many ways operators can manage and mitigate the potential risks as co-author Nathalie Herbelles, head of security and facilitation at the Council, explains.
Nathalie Herbelles, head of security at ACI. Image courtesy: ACI

Image courtesy of
Heidi Vella: The so-called ‘insider threat’ is not a new phenomenon, so why did ACI decide to publish this handbook now?
Nathalie Herbelles: It’s a really important question. We have had a couple of security incidents in the last few years, including the Russian MetroJet flight, which is suspected of crashing due to a bomb explosion, and the Daallo Airlines flight, in which an improvised explosive device killed one passenger and forced an emergency landing in Mogadashu, Somalia. Although investigations are ongoing, it appears both incidents were related to an insider facilitating the attack or bringing the explosive item into the aircraft. In both cases, Islamist extremists claimed responsibility.
So, we knew already insider threats were an issue and a potential threat vector for a terrorist attack. But I think there has been an increasing realisation that we need to look at the range of ways someone might exploit their access to an airport, to either help or carry out an attack on aviation. This could be via access to areas of the airport, to information, to documents or various systems. The problem becomes more acute as more and more of our work includes getting information on mobile devices and from off-site locations.
The threat has a range of different facets and different implications, but there are several measures that can be taken to address them - so that's why we thought now was a good time to produce this handbook.

Image courtesy of ACI
iBeacon technology will provide indoor directions, walking times to gates, lounge access and boarding alerts
Is the risk of insider threats growing?
NH: Not necessarily, but it is something we're realising needs more attention and it’s definitely a reoccurring threat.
There are a range of motivations that might lead someone to carry out harm in an airport. We're not necessarily only talking about casualties, but also people driven by financial gain, or who want to steal money or information for espionage or other purposes. There are also disgruntled people who may have been fired but still have access to the airport and its systems. Our handbook actually shows around 50% of insider cases are driven by financial gain, and only about 20% are driven by ideology.
We also flag in the handbook the potential for mental illness to drive insider attacks - such as the German Wings crash [where all 144 passengers and six crew members were killed in a crash caused deliberately by the co-pilot who had previously been treated for suicidal tendencies] and we intend to look at mental health in more detail in future editions.
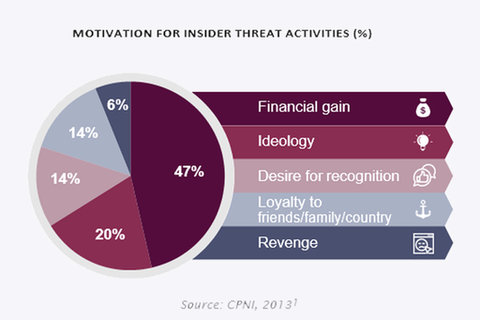
Image courtesy of ACI
What can airport operators do to mitigate the myriad of threats?
NH: There are a range of things, but we really stress that there is not a standalone single measure, such as screening of staff; this is not in itself sufficient, a range of measures to mitigate the threat are needed, because it is so complex, and people have different motivations.
Firstly, however, an airport should conduct a risk assessment because all airports are different and their local risks are different. We have split things into several different categories; personnel and organisational security issues and physical security measures.
For the first, there is a need for pre-employment vetting, such as having proper procedures for recruiting staff. Security culture in airports is very important. Operators need to do awareness training to make sure staff are sensitive to the fact that people - passengers and other staff - might do something wrong and they need to report any suspicious behaviour and have clear channels in place to do that.
On the physical security side, screening, surveillance, canine patrols etc are important. But it’s also paramount to monitor how staff are using badges around security restricted areas. Our Handbook has a dedicated section to cyber security measures because we think having access to information makes an airport very vulnerable. Staff also need to be aware of protecting their passwords and following proper procedures when someone’s employment ends, making sure they cannot access systems with their badge anymore.
iBeacon technology will provide indoor directions, walking times to gates, lounge access and boarding alerts
How can technology help with risk mitigation?
NH: There are a range of technologies now available to help airports, such as video analytics. This technology means that instead of someone having to monitor a screen all the time, systems can automatically flag suspicious behaviour, such as loitering in certain areas or a badge that has been denied access but tried a few times.
Systems can flag this information in a hierarchy of management. This is also possible for monitoring access to computer systems. If someone attempts to access the system a few times, it would be flagged and can be really useful information.
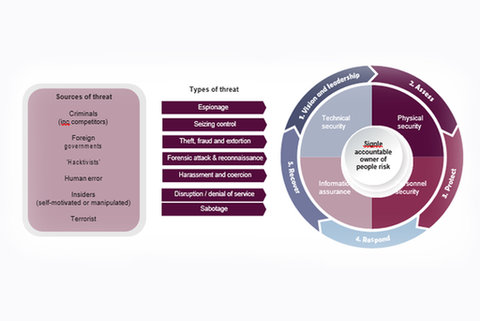
Image courtesy of ACI
How well are airports already implementing these measures?
NH: Airports are very actively mitigating this risk, which is why the handbook was timely; we haven't relied on the input of one airport, but from many airports around the world. We have a Security Committee that has members ranging from Seattle to Amsterdam to China and Singapore, all of whom have contributed some really useful information.
Aggregated these insights result in amazing information because there are different philosophies that in-combination are really useful and can work really well.
For example, in Singapore, there is a system whereby information can be flagged about suspicious behaviour downstream. If a staff member presents themselves at a screening checkpoint and some unusual behaviour has been recorded, that person can be subject to more intense screening.
What are the key takeaways airport operators should be mindful of?
NH: Just that it's a very important issue, and we want all airports to review the measures they have in place and work with their authorities to make sure the regulations are solid. But also, that there is no one-size-fits all, because there is a wide range of insider threats, not just people who are driven by ideology but by financial gain, revenge, disgruntlement. We want airports to make sure the spectrum of measures they have in place can help them address the whole range of threats. And that's why we also need to keep our systems dynamic, flexible and unpredictable.
iBeacon technology will provide indoor directions, walking times to gates, lounge access and boarding alerts